Systems Development,Program Changes, and Application Controls:Substantive Testing Techniques.
Substantive Testing Techniques
Substantive tests are so named because they are used to substantiate dollar amounts in account balances. Substantive tests include but are not limited to the following:
1. Determining the correct value of inventory.
2. Determining the accuracy of prepayments and accruals.
3. Confirming accounts receivable with customers.
4. Searching for unrecorded liabilities.
Before substantive tests can be performed, these data must first be extracted from their host media and presented to the auditor in usable form. The two CAATTs examined in this section assist the auditor in selecting, accessing, and organizing data used for performing substantive tests.
THE EMBEDDED AUDIT MODULE
Embedded audit module (EAM) techniques use one or more programmed modules embedded in a host application to select, for subsequent analysis, transactions that meet predetermined conditions. This approach is illustrated in Figure 17-16.
As the host application processes the selected transaction, a copy of it is stored on an audit file for sub- sequent review. The EAM approach allows material transactions to be captured throughout the audit
period. The auditor retrieves captured transactions at period-end or at any time during the period, thus significantly reducing the amount of work the auditor must do to identify significant transactions for substantive testing.
To begin data capturing, the auditor specifies to the EAM the parameters and materiality threshold of the transactions set to be captured. For example, assume that the auditor establishes a $50,000 materiality threshold for transactions that a sales order processing system has processed. Transactions equal to or greater than $50,000 will be copied to the audit file. From this set of transactions, the auditor will select a subset to be used for substantive tests. The EAM will ignore transactions that fall below this threshold.
Although primarily a substantive testing technique, EAMs may also be used to monitor application controls on an ongoing basis as recommended in the SAS 78/COSO framework. For example, transactions the EAM selects can be reviewed for proper authorization, completeness and accuracy of process- ing, and correct posting to accounts.
Disadvantages of EAMs
The EAM approach has two significant disadvantages. The first pertains to operational efficiency and the second to EAM integrity.
OPERATIONAL EFFICIENCY. From the user’s point of view, EAMs decrease operational performance. The presence of an audit module within the host application may create significant overhead, particularly when the level of testing is high. One approach for relieving this burden from the system is to design modules that the auditor may turn on and off. Doing so will, of course, reduce the effectiveness of the EAM as an ongoing audit tool.
VERIFYING EAM INTEGRITY. The EAM approach may not be a viable audit technique in environments with a high level of program maintenance. When host applications are undergoing frequent changes, the EAMs embedded within the hosts will also require frequent modifications. The integrity concerns raised earlier regarding application maintenance apply equally to EAMs. The integrity of EAM directly affects the quality of the audit process. Auditors must therefore evaluate the EAM integrity. This would be accomplished in the same way as testing the host application controls.
GENERALIZED AUDIT SOFTWARE
GAS is the most widely used CAATT for IT auditing. GAS allows auditors to access electronically coded data files and perform various operations on their contents. ACL and IDEA are currently the leading products, but others exist with similar features. The following audit tasks can be performed using GAS:
1. Footing and balancing entire files or selected data items.
2. Selecting and reporting detailed data contained on files.
3. Selecting stratified statistical samples from data files.
4. Formatting results of tests into reports.
5. Printing confirmations in either standardized or special wording.
6. Screening data and selectively including or excluding items.
7. Comparing two files and identifying any differences.
8. Recalculating data fields.
The widespread popularity of GAS is due to four factors: (1) GAS languages are easy to use and require little IT background on the part of the auditor, (2) GAS may be used on any type of computer because it is hardware independent, (3) auditors can perform their tests on data independent of client IT professional, and (4) GAS can be used to audit the data files of many different applications (in contrast with EAMs, which are application-specific).
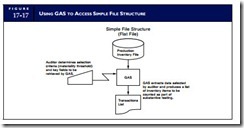
Using GAS to Access Simple Structures
Accessing flat-file structures (such as a text file) is a simple process, as illustrated in Figure 17-17. In this example, an inventory file is read directly into the GAS, which extracts key information needed for the audit, including the quantity on hand, the dollar value, and the warehouse location of each inventory item. The auditor’s task is to perform a physical count of a representative sample of the inventory on hand to verify the existence and value of the inventory. Thus, on the basis of a materiality threshold that the auditor provides, the GAS selects the sample records and prepares a report with the key information.
Using GAS to Access Complex Structures
Gaining access to complex structures, such as virtual storage access method (VSAM) files and object- oriented database files, poses more of a problem for the auditor. Most DBMSs, however, have utility fea- tures that will reformat complex structures into flat files. In such cases, rather than accessing the complex structure directly, an intermediate flat file is produced, which the GAS then accesses. Figure 17-18 shows this technique.
To illustrate the file-flattening process, consider the complex database structure presented in Figure 17-19. The database structure uses pointers to integrate three related files—Customer, Sales Invoice, and
Line Item—in a hierarchical model. It would be difficult, if not impossible, to extract audit evidence directly from a structure of this complexity using GAS. A simpler flat-file version of this structure is illustrated in Figure 17-20. The resulting single text file represents the three record types as a sequential structure with variable length records that GAS can easily access.
Audit Issue Pertaining to the Creation of Flat Files
When auditors rely on client IT personnel to produce a flat file from their database, they run the risk that database integrity will be compromised. For example, if the auditor is confirming accounts receivable, certain fraudulent accounts in the original database may be intentionally omitted from the flat file pro- vided to the auditor. Auditors skilled in relational and object database technology can avoid this problem. Not surprisingly, public accounting firms are aggressively seeking employees with strong computer skills to accompany their accounting training.







Comments
Post a Comment