IT Controls Part II,Security and Access:Electronic Data Interchange (EDI) Controls
Electronic Data Interchange (EDI) Controls
EDI substantially changes the way companies do business and creates unique control issues that accountants need to recognize. Before examining these issues, let’s first review the EDI concept. Figure 16-9 illustrates the data flow through the basic elements of an EDI system that links two trading partners—the customer (Company A) and the vendor (Company B). When Company A wishes to place an order with Company B, Company A’s purchases system automatically creates and sends an electronic purchase
order to its EDI translation software. The translation software converts the purchase order from Company A’s internal format to a standard format, such as ANSI X.12. Next, the communications software adds the protocols to the message to prepare it for transmission over the communication channel. The transmission may be either a direct connection between the trading partners or an indirect connection through a value-added network (VAN). At Company B, the process is reversed, yielding a sales order in Company B’s internal format, which its sales order system processes automatically.
The absence of human intervention in this process presents a unique twist to traditional control problems, including ensuring that transactions are authorized and valid, preventing unauthorized access to data files, and maintaining an audit trail of transactions. The following techniques are used in dealing with these issues.
TRANSACTION AUTHORIZATION AND VALIDATION
Both the customer and the supplier must establish that the transaction being processed is to (or from) a valid trading partner and is authorized. This can be accomplished at three points in the process.
1. Some VANs have the capability of validating passwords and user ID codes for the vendor by matching these against a valid customer file. The VAN rejects any unauthorized trading partner transactions before they reach the vendor’s system.
2. Before being converted, the translation software can validate the trading partner’s ID and password against a validation file in the firm’s database.
3. Before processing, the trading partner’s application software references the valid customer and ven- dor files to validate the transaction.
ACCESS CONTROL
To function smoothly, EDI trading partners must permit a degree of access to private data files that would be forbidden in a traditional environment. The trading partner agreement will determine the degree of access control in place. For example, it may permit the customer’s system to access the vendor’s inventory files to determine if inventories are available. Also, trading partners may agree that the prices on the purchase order will be binding on both parties. The customer must, therefore, periodically access the vendor’s price list file to keep pricing information current. Alternatively, the vendor may need access to the customer’s price list to update prices.
To guard against unauthorized access, each company must establish valid vendor and customer files. Inquiries against databases can thus be validated, and unauthorized attempts at access can be rejected. User authority tables can also be established, which specify the degree of access a trading partner is allowed. For example, the partner may be authorized to read inventory or pricing data but not change values.
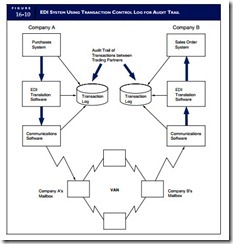
EDI AUDIT TRAIL
The absence of source documents in EDI transactions eliminates the traditional audit trail and restricts the ability of accountants to verify the validity, completeness, timing, and accuracy of transactions. One technique for restoring the audit trail is to maintain a control log, which records the transaction’s flow through each phase of the EDI system. Figure 16-10 illustrates how this approach may be employed.
As the transaction is received at each stage in the process, an entry is made in the log. In the customer’s system, the transaction log can be reconciled to ensure that all transactions the purchases system initiated were correctly translated and communicated. Likewise, in the vendor’s system, the control log will establish that the sales order system correctly translated and processed all messages that the communications software received.
Audit Objectives Relating to EDI
The auditor’s objectives are to determine that (1) all EDI transactions are authorized, validated, and in compliance with the trading partner agreement; (2) no unauthorized organizations gain access to database records; (3) authorized trading partners have access only to approved data; and (4) adequate controls are in place to ensure a complete audit trail of all EDI transactions.
Audit Procedures Relating to EDI
To achieve these control objectives, the auditor may perform the following tests of controls.
TESTS OF AUTHORIZATION AND VALIDATION CONTROLS. The auditor should establish that trading partner identification codes are verified before transactions are processed. To accomplish this, the auditor should (1) review agreements with the VAN facility to validate transactions and ensure that in- formation regarding valid trading partners is complete and correct, and (2) examine the organization’s valid trading partner file for accuracy and completeness.
TESTS OF ACCESS CONTROLS. Security over the valid trading partner file and databases is central to the EDI control framework. The auditor can verify control adequacy in the following ways:
1. The auditor should determine that access to the valid vendor or customer file is limited to authorized employees only. The auditor should verify that passwords and authority tables control access to this file and that the data are encrypted.
2.The trading agreement will determine the degree of access a trading partner should have to the firm’s database records (such as inventory levels and price lists). The auditor should reconcile the terms of the trading agreement against the trading partner’s access privileges stated in the database authority table.
3. The auditor should simulate access by a sample of trading partners and attempt to violate access privileges.
TESTS OF AUDIT TRAIL CONTROLS. The auditor should verify that the EDI system produces a transaction log that tracks transactions through all stages of processing. By selecting a sample of transactions and tracing these through the process, the auditor can verify that key data values were recorded correctly at each point.




Comments
Post a Comment