Problems on Systems Development,Program Changes, and Application Controls.
Problems
1. INPUT VALIDATION
Describe the types of application control used for the contributes to ensuring the reliability of data. Use the following format.
following data in a payroll system.
a. Employee name
b. Employee number
c. Social Security number
d. Rate per hour or salarye. Marital status
f. Number of dependents
g. Cost center
h. Regular hours worked
i. Overtime hours worked
j. Total employees this payroll period
2. COMPUTER FRAUD AND CONTROLS
Although the threat to security via external penetration is often seen as the greatest threat, many threats are internal. Computer frauds include (1) input manipulation,(1) program alteration, (3) file alteration, (4) data theft, and (5) sabotage.
Required
Explain how each of these five types of fraud is com- mitted. Also, identify a method of protection against each without using the same protection method for more than one type of fraud. Use the following format.
3. PROCESSING CONTROLS
A well-designed system can prevent both intentional and unintentional alteration and destruction of data. These data controls can be classified as (1) input controls, (2) processing controls, and (3) output controls
Required
For each of the three control categories listed, provide two specific controls and explain how each control
4. INPUT CONTROLS AND DATA PROCESSING
A catalog company has hired you to computerize its sales order entry forms. Approximately 60 percent of all orders are received over the telephone, with the remain- der received by either mail or fax. The company wants the phone orders to be input as they are received. The mail and fax orders can be batched together in groups of 50 and submitted for keypunching as they become ready. The following information is collected for each order:
• Customer number (if customer does not have one, one needs to be assigned)
• Customer name
• Address
• Payment method (credit card or money order)
• Credit card number and expiration date (if necessary)
• Items ordered and quantity
• Unit price
Required
Determine control techniques to make sure that all orders are entered accurately into the system. Also, discuss any differences in control measures between the batch and the real-time processing.
5. AUDIT PLAN
Rainbow Paint Company, a medium-sized manufacturing firm, has no internal auditing department. It recently hired a new accounting firm to perform the external audit.
Required
Outline an audit plan to examine operating system con- trol, program maintenance controls, and organizational system controls. Include in your plan the audit objectives, exposures, necessary controls, and test of controls. Also include any documentation the auditors should request.6. AUDIT PLAN
The auditors for Golden Gate Company have a gut feeling that liabilities may be unrecorded. Their initial suspicions stem from a radical decline in accrued liabilities from last year. Golden Gate’s records are all computerized.
Required
Devise a plan to search the data files to perform a sub- stantive test for identifying unrecorded liabilities.
7. RISK IDENTIFICATION AND PLAN OF ACTION
Two years ago, an external auditing firm supervised the programming of embedded audit modules for Previts Office Equipment Company. During the audit process this year, the external auditors requested that a transaction log of all transactions be copied to the audit file. The external auditors noticed large gaps in dates and times for transactions being copied to the audit file. When they inquired about this, they were informed that increased processing of transactions had been burdening the mainframe system and that operators frequently had to turn off the EAM to allow the processing of important transactions in a timely fashion. In addition, much maintenance had been performed during the past year on the application programs.
Required
Outline any potential exposures and determine the courses of action the external auditors should use to proceed.
8. RISK IDENTIFICATION AND PLAN OF ACTION
The internal auditors of Brown Electrical Company report to the controller. Because of changes made in the past year to several of the transaction processing pro- grams, the internal auditors created a new test data set. The external auditors requested that the old data set also be run. The internal auditors embarrassingly explained that they overwrote the original test data set.
Required
Outline any potential exposures and determine the courses of action the external auditor should take.
9. RISK IDENTIFICATION AND PLAN OF ACTION
As the manager of the external audit team, you realize that the embedded audit module only writes material invoices to the audit file for the accounts receivable confirmation process. You are immediately concerned that the accounts receivable account may be substantially overstated this year and for the prior years in which this EAM was used.
Required
Explain why you are concerned because all ‘‘material’’ invoices are candidates for confirmation by the customer. Outline a plan for determining if the accounts receivable are overstated.
10. AUDIT OBJECTIVES AND PROCEDURES
You are conducting substantive tests on the accounts receivable file to verify its accuracy. The file is large, and you decide to test only a sample of the records. Because of the complexity of the database structure, you cannot access the database directly. The client’s systems programmer uses a utility program to write a query that produces a flat file, which he provides for testing purposes.
Required
Discuss any concerns you would have as an auditor and any actions you would take.
11. SYSTEMS DEVELOPMENT AND PROGRAM CHANGES
Avatar Financials, Inc., located on Madison Avenue in New York City, is a company that provides financial advice to individuals and small to mid-sized businesses. Its primary operations are in wealth management and financial advice. Each client has an account where basic personal information is stored at a server within the main office in New York City. The company also keeps the in- formation about the amount of investment of each client on a separate server at their data center in Bethlehem, Pennsylvania. This information includes the total value of the portfolio, type of investments made, the income structure of each client, and associated tax liabilities.
Avatar decided to purchase software for asset management from specialized vendors. This software allows them to run analytics on the portfolios and run detailed simulations of market trends and is called Siman (SIMulation ANalytics). V-Dot Solutions, another contractual company that is customizing and installing Siman, has sent a team of six systems analysts to carry out this task. They anticipate additional hardware installations to run the simulation analytics on Siman.
V-Dot’s setup requires them to train two people from Avatar who will be responsible for minor issues and ba- sic maintenance of the system. Special consultants from V-Dot will deal with major problems and issues. It takes 4 weeks to completely have the system operational and integrated into Avatar’s existing computer system. The testing phase of the project has been readjusted to allow the two employees of Avatar to run these tests and ensure compatibility.
A year after the installation of the simulation soft- ware Siman, Avatar finds it very useful. To upgrade the systems to the next level, they decide to go to another data source company for a raw market data feed that will be used to run the simulations. However, this requires changes to the source code of Siman. Fortu- nately, within its analytics department that uses Siman, Avatar has two programmers who are well versed in the programming language that Siman was written in. These programmers are able to implement the changes that will allow Siman-II to use the new data feed.
To remain competitive, Avatar has placed the programmers under a tight time constraint. To expedite the process, the documentation process is shortened with the intention that it will be looked into once the systems are running. The programmers also will be deployed back to the maintenance operations once the project is complete. The contract with Siman’s original vendor, V-Dot, has expired and the company does not want to extend their maintenance services for another year. Instead, it believes that these two programmers will be able to perform the same tasks for less money.
Required
a. Discuss the major internal control issues in Avatar’s systems development approach.
b. Comment on the duties the two programmers of Av- atar perform. Are systems maintenance and program development extensions of the same responsibility?
c. Identify potential issues that might arise due to weak internal controls.
12. COMPUTER-ASSISTED AUDIT TOOLS AND TECHNIQUES (CAATTS)
Required
a. Explain the advantages of using GAS to assist with audits and give several examples of how it may be used.
b. Describe the audit purpose facilitated and the procedural steps to be followed when using the following CAATTs.
1. ITF
2. EAM
3. parallel simulation
13. AUDIT OF SYSTEMS DEVELOPMENT
The Balcar Company’s auditors are developing an audit plan to review the company’s systems development pro- cedures. Their audit objectives are to ensure that
1. the system was judged necessary and justified at various checkpoints throughout the SDLC.
2. systems development activities are applied consis- tently and in accordance with management’s policies to all systems development projects.
3. the system as originally implemented was free from material errors and fraud.
4. system documentation is sufficiently accurate and complete to facilitate audit and maintenance activities.
The following six controllable activities have been identified as sources of audit evidence for meeting these objectives: systems authorization, user specification, technical design, internal audit participation, program testing, and user testing and acceptance.
Required
a. Explain the importance of each of the six activities in promoting effective control.
b. Outline the tests of controls that the auditor would perform in meeting audit objectives.
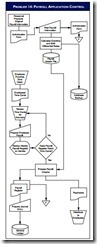
14. PAYROLL APPLICATION CONTROL
Using this supplemental information, analyze the flow- chart in the diagram for Problem 14.
• The personnel department determines the wage rate of all employees. To start the process, personnel sends the payroll coordinator, George Jones, an authorization form in order to add an employee to the payroll. After Jones enters this information into the system, the computer automatically determines the overtime and shift differential rates for the individual, updating the payroll master files.
• Employees use a time clock to record the hours worked. Every Monday morning, George Jones col- lects the previous week’s time cards and begins the computerized processing of payroll information to produce paychecks the following Friday. Jones then reviews the time cards to ensure that the hours worked are correctly totaled; the system determines overtime and/or any shift differential.
• Jones performs all other processes displayed on the flowchart. The system automatically assigns a sequential number to each payroll check produced. The check stocks are stored in a box next to the computer printer to provide immediate access. After the checks are printed, an automatic check-signing machine signs them with an authorized signature plate that Jones keeps locked in a safe.
• After the check processing is completed, Jones distributes the checks to the employees, leaving the checks for the second- and third-shift employees with the appropriate shift supervisor. Jones then notifies the data processing department that he is finished with his weekly processing, and data processing makes a backup of the payroll master for storage in the computer room.
Required
Identify and describe:
a. Areas in the payroll processing system where the internal controls are inadequate.
b. Two areas in the payroll system where the system controls are satisfactory.




Comments
Post a Comment